In the past ten years, the number of internet users has almost doubled. It’s now a staple of daily life for almost 70% of the global population.1
Alongside this expansion, awareness and use of Open Source Intelligence (OSINT) has also grown. There is now more publicly available information than ever before – and more organisations are seeking to leverage it.
In this article, we’ll explore what OSINT means today, which organisations should be using it and the best practices every investigator should know.
What is OSINT?
Open Source Intelligence (OSINT) is the targeted collection and analysis of publicly available or licensable data to produce actionable insights.
OSINT is often a highly digital discipline. After all, the growth of the internet means there’s now more publicly available data than ever before.
However, OSINT investigators aren’t limited to online data. Many investigators used OSINT techniques before the internet even existed, with practices dating back to as early as 1863.2
What's the difference between OSINT and OSINF?
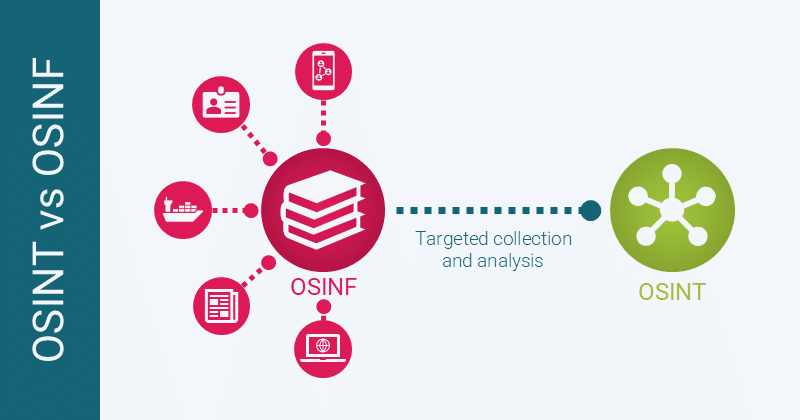
An important step in defining OSINT is understanding the difference between OSINT (Open Source Intelligence) and OSINF (Open Source Information).
OSINF is publicly or commercially available information from sources such as news publications, social media sites and corporate registries. Such data is often biased and unlikely to contain useful insights on its own.
OSINT is the product of collecting, combining and analysing OSINF. It provides actionable intelligence and illuminates insights not always evident in the raw data itself.
As open source intelligence has grown in popularity, more people are misusing these terms. However, knowing the difference is crucial to making effective use of OSINT. You can read more about the difference between OSINT and OSINF in our article, How reliable is OSINT?
Who is using OSINT today?
OSINT is traditionally a government discipline. Today, though, government organisations aren’t the only ones using it to produce valuable insights.
The growth of the internet and influential investigations from organisations like Bellingcat have both played a part in spreading awareness of OSINT. Now, a wide range of organisations within public sector and beyond are using this intelligence technique. To give an idea of scale, the OSINT market size was valued at $14.85 billion in 2024. Plus, opportunities for further growth remain: the market size is forecast to grow to $49.39 billion in 2029.3
Below, we’ll explore how different organisations are using OSINT today and what they can do to achieve greater effectiveness.
Government and Law Enforcement
Open source intelligence continues to be a key source of intelligence for government and law enforcement alike. Investigators rely on this technique in use cases from border security to counter-fraud.
As the internet has expanded, so too have the insights available from OSINT. It’s now possible for public sector organisations to gain a more direct view into criminal activity using OSINT. For example, practitioners can monitor forums on the dark web to identify and disrupt the sale of illegal goods.
Financial Services
With financial crime growing more complex, banks need to do more to ensure they’re getting an accurate picture of risk. OSINT helps them achieve this, allowing them to spot risk that’s hidden from internal sources and official databases.
From a compliance perspective, OSINT has yet to become a formal regulatory requirement. However, regulations are certainly tightening. Recent regulations like the EU AML Package place a greater focus on enhanced due diligence and truly understanding business connections. Practically, such in-depth understanding is difficult to achieve without OSINT – suggesting this type of investigation may soon become a requirement. Firms adopting open source intelligence now will stay ahead of any such compliance changes.
Find out how OSINT can be applied to AML by watching our free webinar series or reading the handbook.
Corporates
New risks and threats are emerging for businesses every day. OSINT has a crucial role to play in understanding and countering these – for example:
- Due diligence: Supply chains are becoming more complex. Yet, new regulations like the EU CSDDD require businesses to have a better understanding of them than ever before. OSINT helps illuminate hidden risk and connections, making it an ideal tool for such investigations.
- Brand protection: Many counterfeits of branded products are now sold online – from designer goods to pharmaceuticals. OSINT is crucial in pinpointing those responsible and preserving brand credibility.
- Security: Mapping and collecting information on threats allows for more informed mitigation measures.
- Insider threat identification: OSINT is ideal for gaining an accurate picture of networks and connections. When it comes to understanding insider threat risk, such information is crucial.
Media Outlets
Media outlets are making increasing use of OSINT to supplement their findings. This includes OSINT-specialist organisations like Bellingcat, investigative journalism channels like OCCRP, and even mainstream outlets like the BBC.
In some cases, media outlets have used OSINT to become the first to uncover certain large-scale scandals. This proves the value of OSINT in today’s digital world and the need for other organisations to catch up. Where an organisation is unable to spot risk within its ranks before an external party does so, it can cause serious reputational damage.
What sources does OSINT use?
One of the unique benefits of OSINT is the range of sources it offers to investigators. OSINT can be drawn from sources including:
- News media: From large international publications to small local outlets, news media provides a range of perspectives on current events. Investigators using these sources need to be aware of potential bias and assess reliability accordingly.
- Corporate registry data: Unravelling corporate connections is key to many OSINT use cases. Much corporate records data is available for free, however a paid-for source can often provide deeper coverage.
- Publicly available social media: From revealing personal connections to lifestyle information, social media has become an important resource over the past decade. Investigators must ensure they’re only using data that is publicly available, though. Otherwise, the investigation may stray beyond the boundaries of OSINT and become a breach of privacy.
- Dark web: Accessing this source can be risky, but it’s important for cases that require direct insight into criminal activity. For example, law enforcement might use dark web data to identify the sale of illegal drugs and weapons. Certain tools make it safer and easier to access this data.
When working with these sources, it’s important to remember that they’re just information, not intelligence. Investigators need to combine data from various sources and systematically analyse it before it can be considered OSINT.
How to use OSINT in practice
By now, we’ve defined what open source intelligence is and who is – or should be – using it. But what do investigators need to be aware of to ensure they’re using OSINT as effectively as possible?
Before exploring exciting sources or trying out the latest tool, it’s important to have a firm grasp on OSINT fundamentals. Otherwise, an investigation runs the risk of being inaccurate or even unethical.
What is the intelligence cycle?
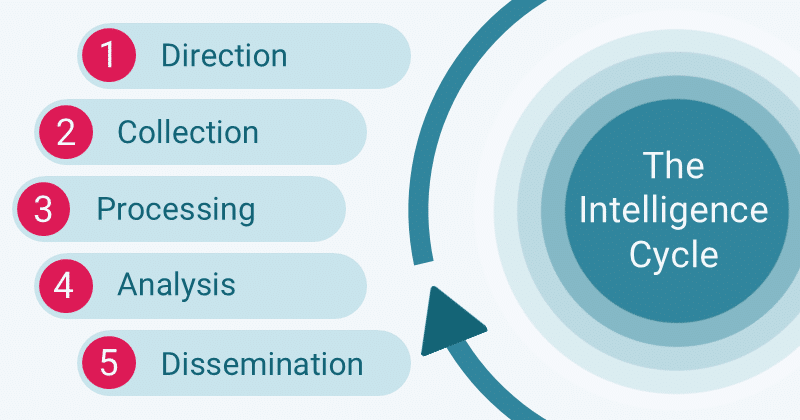
The intelligence cycle is an investigative framework that ensures operations remain targeted, ethical and effective. It’s a fundamental technique for any OSINT investigator, regardless of their level of experience.
Below, we’ll walk through each step of the intelligence cycle and why it’s important.
Step one: Direction
The first stage, direction, focuses on defining the scope of an investigation. To complete this stage, investigators must:
- Outline the purpose of this investigation. Which question are you aiming to answer or what intelligence gap are you hoping to fill?
- With this in mind, define the scope for the investigation. What sources would be appropriate and ethical to access based on the question you’re answering? How ‘big’ do you expect this investigation to be?
Completing the direction stage means you’re laying the groundwork for a successful investigation. It’s absolutely essential for ensuring the investigation remains targeted and ethical later on.
Step two: Collection
Having identified subjects of interest and appropriate data sources in the direction stage, the investigator can now begin collecting data.
As we mentioned previously, there are many sources available to OSINT investigators. This can make the collection stage time-consuming when practiced manually. It can even be prone to human error, as you may misplace or misattribute information as you switch between sources.
Technology can speed up this stage, allowing investigators to view multiple sources in one place and automatically logging data. However, it’s important to retain human oversight. Investigators must understand where data comes from and only collect it in a targeted manner.
Step three: Processing
At the processing stage, the investigator refines the information they’ve gathered. The goal is to present the data in a clear, digestible format so that it’s easier to analyse later on. This might include visualising the data to get a better understanding of connections or putting it in a table to compare values such as dates.
Much of this stage can be automated without taking any key decisions away from the investigator. As OSINT technology continues to develop, this stage will be a key focus.
Step four: Analysis
This is the stage where data becomes intelligence. Here, investigators use their valuable analytical skills to draw meaning from the data they’ve collected and processed. Having successfully completed the previous stages, they can now uncover new insights faster and with more clarity.
Step five: Dissemination
Finally, investigators present their findings in a digestible format, allowing them to share the results of their investigation. What this looks like depends largely on the purpose of the investigation and who the investigator is. Often, though, it will take the form of a report.
What should you consider when selecting an OSINT tool?
The expansion of the internet has brought new opportunities for OSINT investigators – but also new challenges. From overwhelming volumes of data to disparity of sources, investigators face increasing barriers to success.
Luckily, innovative technology can help. For example, visualisation tools make analysis faster and more intuitive, and search platforms often allow investigators to collect data from multiple sources at once. Here are some key factors investigators should consider when picking an OSINT tool:
- Human oversight: Whilst automation can be helpful in speeding up investigations, technology shouldn’t make any important decisions. Otherwise, ethics and accuracy may be impacted.
- Alignment with existing workflows: Supported by technology, investigators should still make use of the intelligence cycle. Look for tools that fit with your current processes and allow you to follow best practices.
- Data provenance: Do you understand where the data you’re accessing via this tool comes from? Are you sure it’s accurate, publicly available and ethically collected?
- Solutions: It’s important to establish whether this tool solves your main challenges. Sometimes, integrating unnecessary tooling can create more complexity.
If you’re looking to enhance your investigations with an all-in-one platform, speak to us today.
FAQs
What does OSINT stand for?
OSINT stands for Open Source Intelligence.
What is OSINT?
OSINT is the targeted collection and analysis of publicly available data to draw actionable insights.
What is OSINT used for?
Organisations such as banks, government agencies and media outlets use OSINT to derive insights not available through other sources of intelligence. It’s a key tool for use cases from anti-money laundering to investigating organised crime.
What is the difference between OSINF and OSINT?
OSINF (open source information) is publicly available data, found in sources like newspapers, online forums and (public) social media. It’s sometimes biased and unregulated. On the other hand, OSINT is the targeted use of this data to produce actionable intelligence. When conducted by an experienced investigator, it’s reliable and accurate.
What are the different types of OSINF?
-
News and media
-
Corporate records
-
Social media
-
Dark web data
-
Search engine data
How do you use open source intelligence?
Investigators using OSINT should follow best practices such as the intelligence cycle to maintain effectiveness and ethics. They should ensure operations are highly targeted and only draw upon publicly or commercially available data.
How do I choose the right OSINT tool for the data I’m using?
1. Explore and understand what's available to you. There are multiple OSINT tools to choose from depending on your requirements.
2. Book a demo. Get a feel for the technology and how it could benefit you in the long term.
3. Have a discussion. After your demo, we can answer any questions you have about the software and how your organisation could benefit.
Footnotes
- https://www.statista.com/topics/1145/internet-usage-worldwide/#topicOverview
- https://www.tandfonline.com/doi/full/10.1080/16161262.2023.2224091#d1e1533
- https://www.thebusinessresearchcompany.com/report/open-source-intelligence-global-market-report



