Illuminate Intelligence in Open Source Data
Turn open source data into intelligence with Videris, the leading OSINT solution for public and private sector investigators.
Collect, analyse and visualise all your investigation data in one platform to produce actionable insights, fast.

We are the experts in enterprise investigations, intelligence and data.
From automating EDD reports to enhancing dynamic complex investigations, we help the public sector, financial institutions and corporations to manage risk, and fight economic, serious and organised crime.
OSINT for the enterprise
Open Source Intelligence is the use of publicly available or licensable data to draw actionable intelligence insights.
Open source data is freely available and easy to access – but turning disparate data into intelligence can be challenging.
As criminal tactics grow more complex, unlocking the full power of Open Source Intelligence is crucial. Videris makes this possible for any organisation.

Increase investigative impact
Videris uses explainable AI and intelligent automation to speed up traditionally manual investigation processes.
From streamlined data collection, to AI-powered analysis and automated network visualisation – Videris modernises organisations’ approach to OSINT, increasing investigations teams’ impact.

Who we work with

Public sector
From identifying fraud, to mapping organised crime groups, to understanding trafficking networks, government and law enforcement use Videris to find and prevent societal harm.
As crime becomes increasingly digitalised, effective OSINT has never been more important.
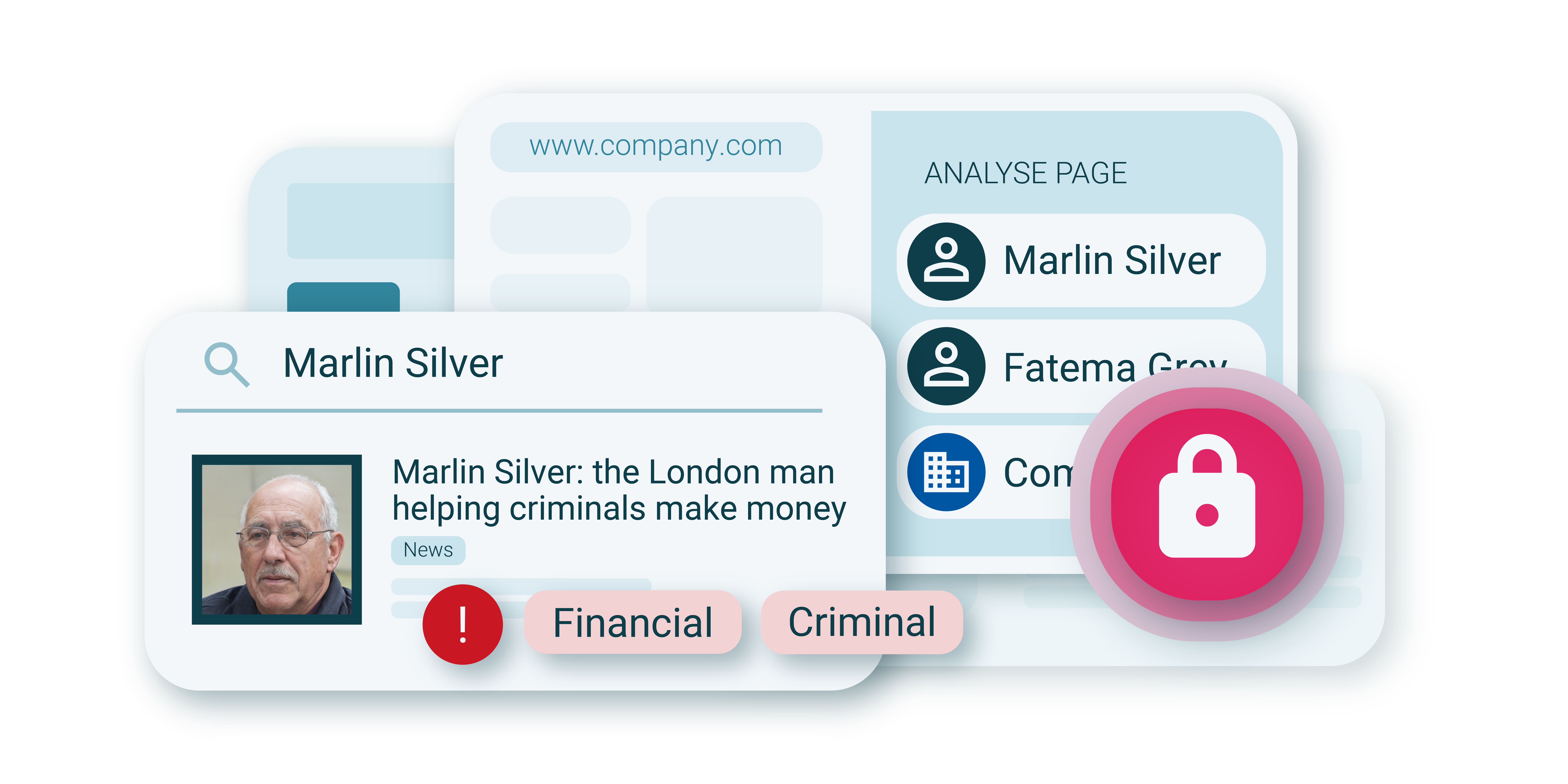
Financial institutions
As financial crime grows more complex and compliance requirements tighten, financial institutions need to do more with fewer resources.
FIs are using Videris to increase investigation efficiency while gaining a fuller picture of clients, counterparties and their networks in AML, EDD and sanctions cases.
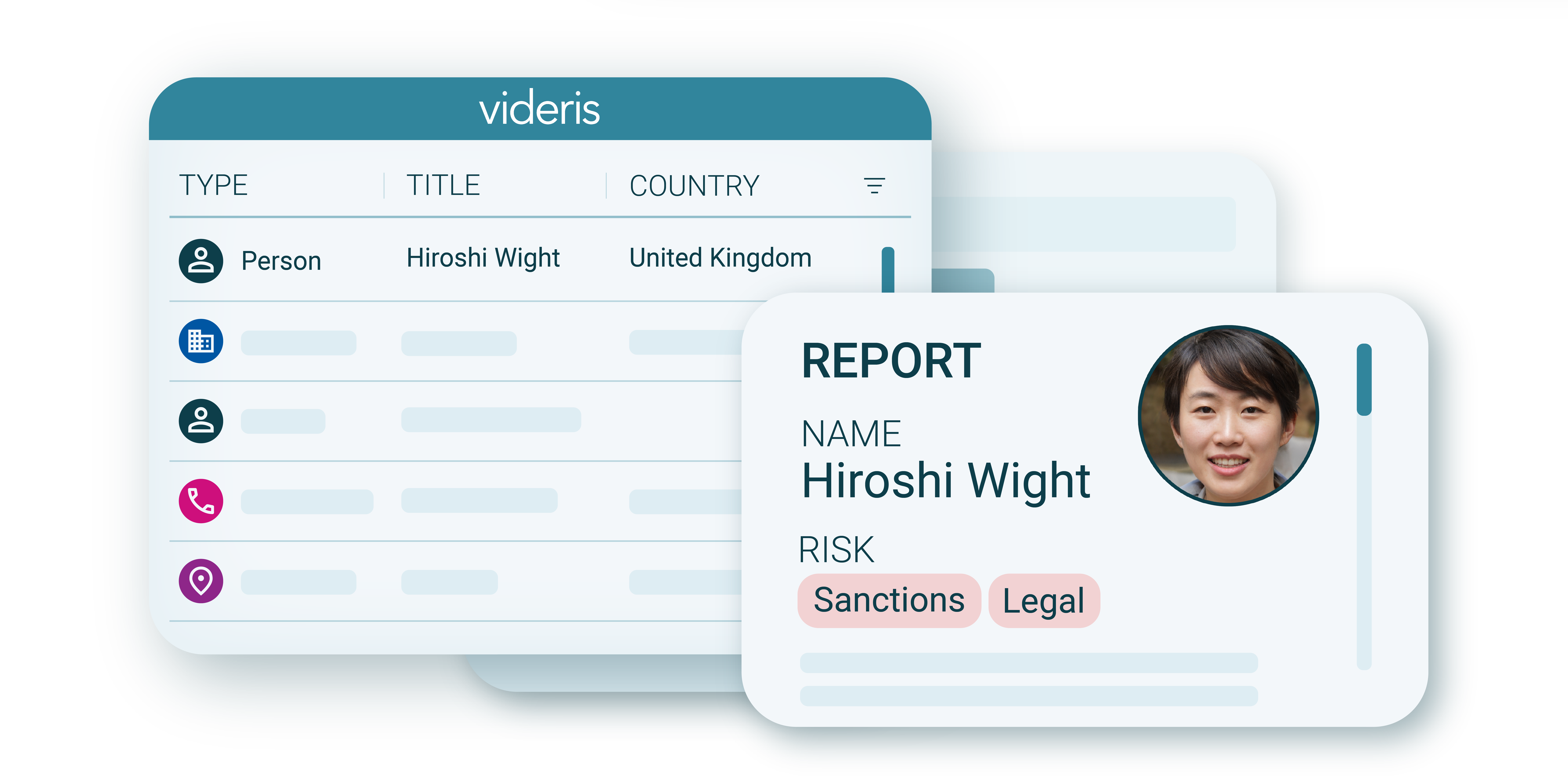
Corporations
Businesses today are facing a multitude of challenges: from insider threat, to supply chain risk and brand theft.
Large corporates use Videris to find the perpetrators behind these crimes, reclaim funds and avoid future losses.
Why Videris?
Streamline processes
With Videris, teams can automate manual processes, consolidate data access and reduce the friction of switching between data sources.
Benefit from fast return on investment and better resource management, with organisations reporting working up to 5x more efficiently.
Unlock OSINT
Future-proof your organisation’s investigation processes, plug intelligence gaps and stay ahead of criminals by investing in OSINT.
Videris provides access to a multitude of data sources, ensuring you won’t face barriers in accessing the data you need.
Improve investigation outcomes
Never miss a key insight, spot hidden risks and demonstrate true effectiveness in fighting crime without increasing resources.
Videris is context-aware and enhances human investigative skills, so no vital intelligence is missed.
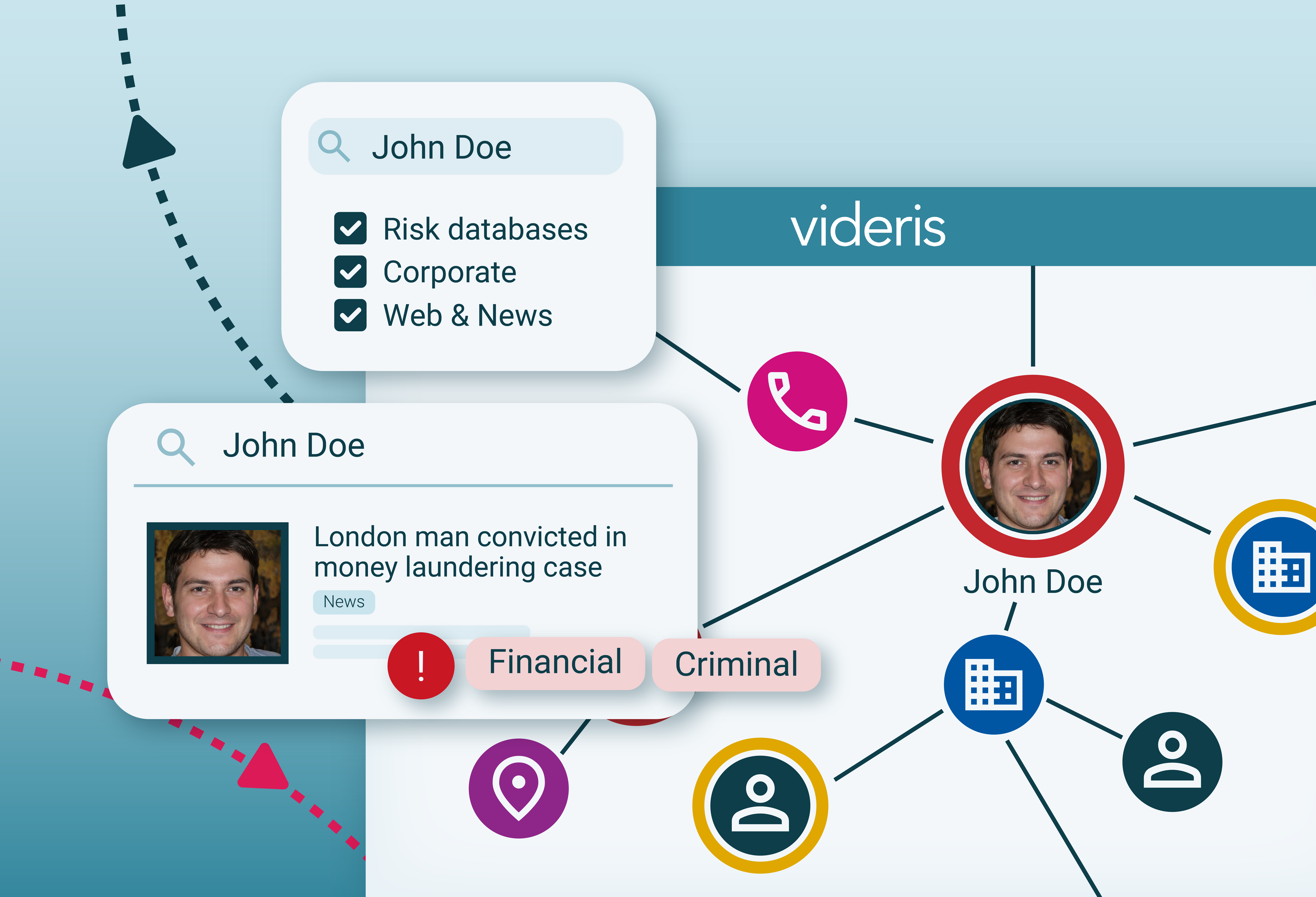
Blackdot Videris
Designed by investigators, for investigators, Videris is an OSINT platform built for the enterprise.
Organisations can benefit from total automation for higher volume cases in AI-driven Videris Automate, then escalate to Videris Investigate for analyst-driven investigation.
An intuitive platform with minimal time-to-value, both experienced and novice investigators can use Videris to increase efficiency and draw maximum value from OSINT.
Benefit from custom inbuilt federated search, network analysis tools, secure browsing capability and even the ability to integrate your own data sources.
OSINT Insights
Get OSINT insights and Blackdot news by reading our blog.

What we learnt from Counter Fraud: Barriers to transitioning from detection to prevention
Last week, our team attended the GovNet Counter Fraud Conference 2026. With topics of discussion ranging from understanding data to...
By Annie Finlay

Big data, network analysis and the right tools in OSINT with Chris P.
Chris P, Head of Intelligence at Blackdot, joined the latest episode of From the Source, the Blackdot podcast. He discussed his diverse...
By Rebecca Lindley

Top 3 insights for Financial Services from The State of OSINT
Financial services (FS) investigation professionals are uniquely positioned to disrupt the flow of funds to criminals. The stakes are high:...
By Charli Foreman